Welcome to my second article on “Mobile Forensics”. You can find the Part 1 here.
The second step in the forensic process is Acquisition. This is referring to retrieval of data from the device, unlike the process of acquiring a forensic image of PC which is a well-documented and usually straightforward task for a forensic examiner. The world of mobile device forensics is a complicated one. So, before I dive deep into the acquisition we want to look more at the Smart “SIM” Card Standards. “Boring! I know !”.

Smart Card Standards
- ISO 7816-1: Physical characteristics,
- ISO 7816-2: Electrical contacts,
- ISO 7816-3: Electrical interface, (T=0: Byte-oriented protocol T=1: Block-oriented protocol)
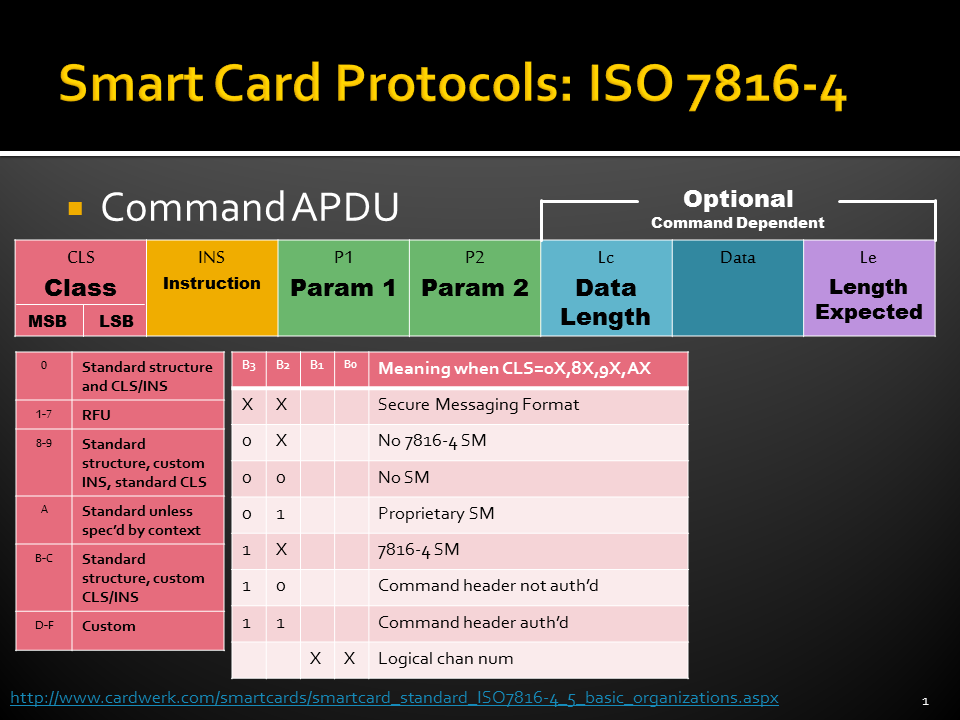
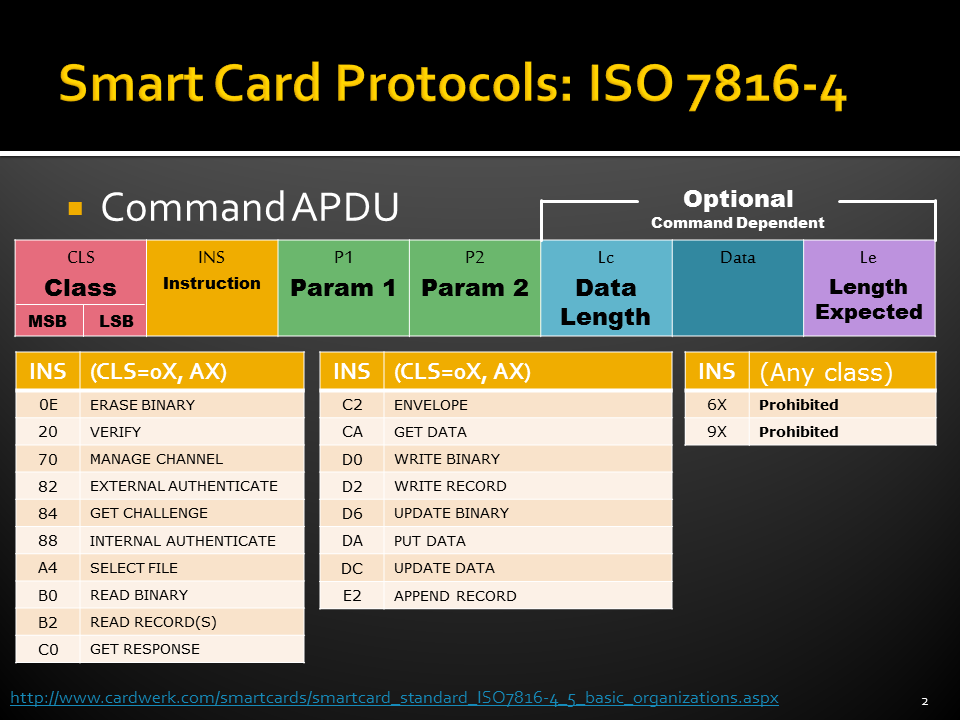
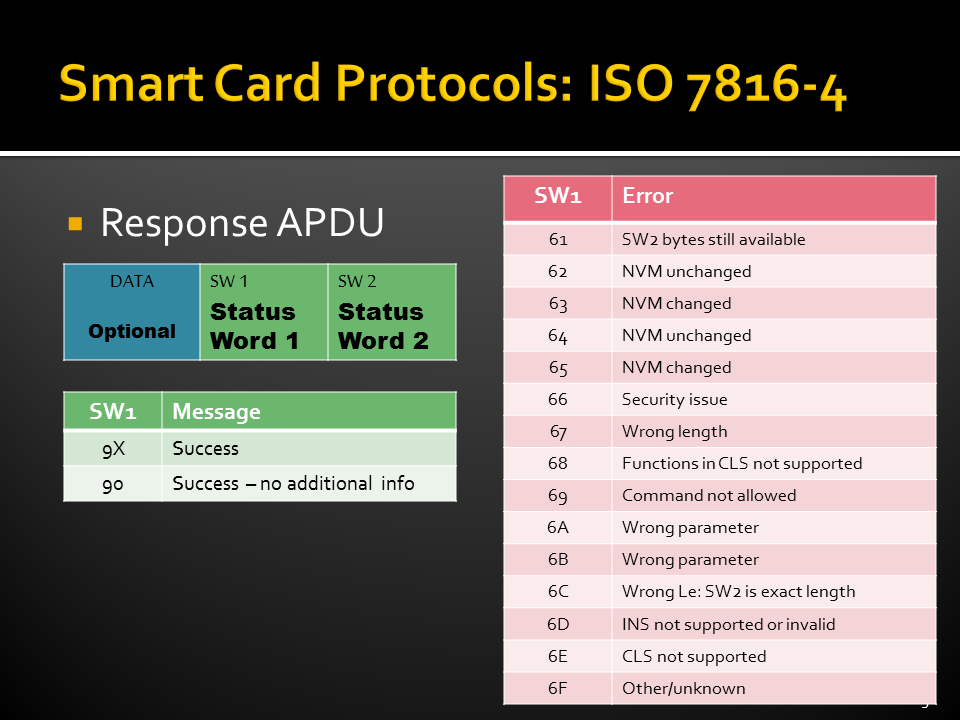
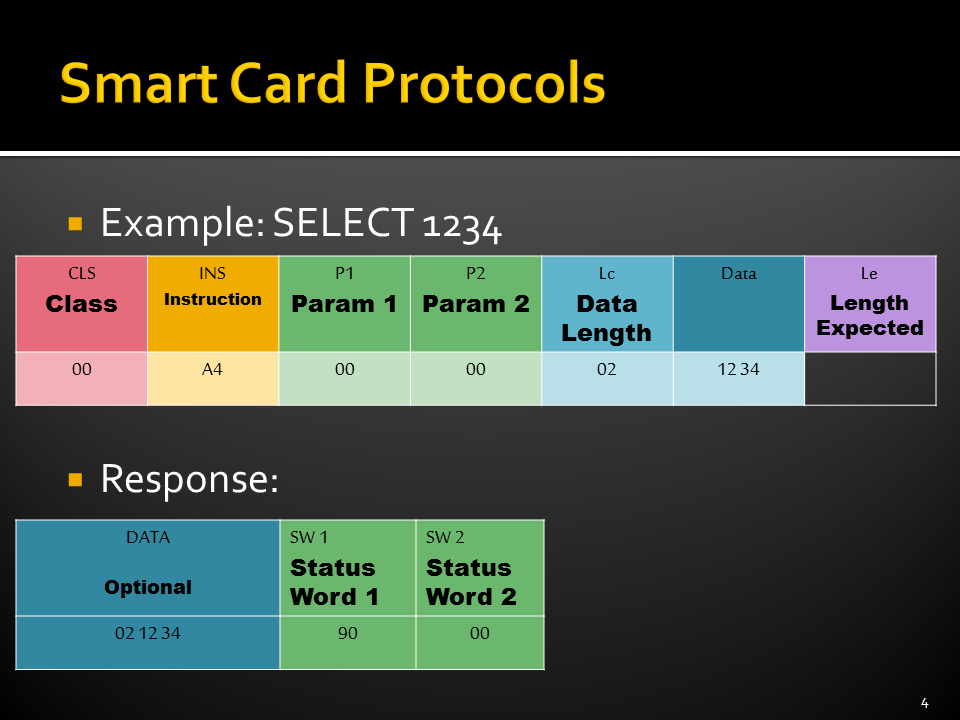
- ISO 7816-4: Standard commands, Application Protocol Data Units (APDUs),
- ISO 14443-4: “T=CL”: APDUs over RFID
The UICC
The UICC (Universal Integrated Circuit Card) is a smart card which contains account information and memory that is used to enable GSM cellular telephones.
One of the applications running on the smart card is the SIM. The SIM (Subscriber Identity Module) contains both a processor (CPU) and an operating system which is either native (proprietary, vendor specific) or Java Card (a subset of the Java programming language).
SIMs also have Electrically Erasable Programmable Read Only Memory (EEPROM), Random Access Memory (RAM) for controlling program execution, and persistent Read Only Memory (ROM) which stores user authentication, data encryption algorithms, the operating system, and other applications. Communication between the SIM card and the handset is via a serial interface.
Although SIM-based Applications are not common in the EU and US in many parts of the world they are a lifeline. In fact, it is the norm to pay for a taxi ride using your mobile phone in Somalia or Kenya; mobile payment services like EVC plus and M-PESA alone have over fifteen million subscribers.
SIM Card – Evolution & Types
SIM cards have been in the industry since 1991 and are classified in a range of SIM card sizes; Full-Size SIM, Mini-SIM, Micro-SIM, Nano-SIM, and embedded SIMs, respectively. A variety of SIMs emerged with the introduction of smartphones to the market.

Storage File System of SIM Cards
A SIM is organised in a hierarchical tree structure. It consists of the following three types of elements: MF, DF, and EF which are the Master, Dedicated, and Elementary File systems, in that order. MF is the root of all file systems and has DF and EF as its subordinate directories. These file systems hold on to various structured data as the sequence of either data bytes, regularly used records of fixed size, or limited size of records, respectively.
Smart Card File System (ISO 7816-4)

While all the files have headers, only the EFs contain data. The first byte of the header identifies the file type. Headers contain the security and meta-information related to the structure and attributes of the file, such as length of the record. The body of the EFs contains information related to the application. Files can be either administrative or application specific and access to stored data is controlled by the operating system.
SIM Card Forensic Imaging
SIM Card imaging is a procedure that creates an exact replica image of your SIM Card content to be processed during SIM card forensics. The technique is necessary in order to keep original evidence intact while the replica image is being used for repeated analysis. I will do a future blog and entire work-through of what’s required in this process.
Tip – check out a great tool called Last-SIM which gives details about a phone’s previously inserted SIM cards.
To Be Continued
Disclaimer
Tools are mentioned in this series to illustrate concepts and techniques, not to indicate that a particular tool is best suited to a particular purpose. Digital investigators must take responsibility to select and evaluate their tools. Any legal issues covered in this text are provided to improve understanding only and are not intended as legal advice. Seek competent legal advice to address specifics of a case and to ensure that nuances of the law are considered.
